If you’ve never been a victim of identity theft, consider yourself lucky. Millions of people have had to fight their way out of serious financial trouble because of one wrong person getting hold of their personal information.
Identity theft is possibly the worst cybercrime of all, one that can easily destroy a lifetime’s worth of reputation, finances, and credit history, which can take years to recover from.
A 2017 study by Javelin Strategy & Research found that about 15.4 million consumers in the U.S are victims of identity theft in one form or another, with an estimated total of $16 billion stolen – and the numbers keep rising each year.
If you’ve fallen victim to identity theft, this resource is your survival guide on how to gain back control, steps to recover from fraud and identity theft, as well as many useful tips and helpful information to protect yourself from being a victim of cybercrime in the future.
Identity Theft: The Facts
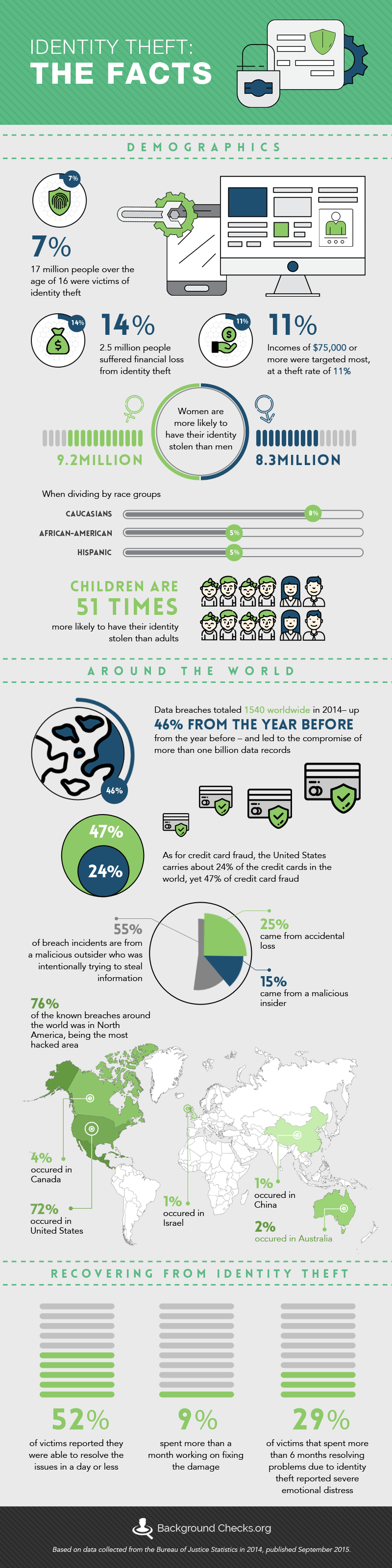
- Statistics from the Bureau of Justice Statistics states that about 7% of people over the age of 16 were victims of identity theft. That may not seem like a lot, but when you take into account that there were 242 million people over 18 in the US in 2014, that would mean over 17 million people were taken advantage of.
- The bureau also reports that 14%, or 2.5 million, suffered financial loss from identity theft.
- Women are more likely to have their identity stolen than men, at 9.2 million women compared to 8.3 million men.
- When dividing by race groups, Caucasians have a rate of 8%, African Americans are about 5% – as are Hispanics. Incomes of $75,000 or more annually were targeted most, at theft rate of 11%.
- 52% of victims reported they were able to resolve the issues in a day or less, but 9% spent more than a month working on fixing the damage done. 29% of victims that spent more than 6 months resolving problems due to identity theft reported severe emotional distress.
- Surprisingly, children are 51x more likely to have their identity stolen than adults would be. They are vulnerable to someone who might try to manipulate them because they don’t realize the risk. The vast majority of child identities stolen are used to open credit accounts and to substantiate loans, often by family members or relatives. Parents usually warn children about sexual predators and being modest on social media, but what they don’t usually think about is people who might pray on their naivety online and get them to give up pertinent information that would compromise their identity security.
Statistics Around The World
- According to NASDAQ, “Data breaches totaled 1,540 worldwide in 2014 – up 46 percent from the year before – and led to the compromise of more than one billion data records.”
- 55% of breach incidents are from a malicious outsider who was intentionally trying to get in and steal information. 25% came from accidental loss and 15% came from a malicious insider.
- The most hacked area was North America, accounting for 76% of the known breaches around the world. 72% occurred in the United States alone. The United Kingdom accounts for 8% of the breaches, Canada carries 4%, Australia accounts for 2%, and Israel and China both carry 1% of the burden.
- As for credit card fraud, the United States only carries about 24% of the credit cards in the world, yet 47% of credit card fraud. Countries that have adopted the EMV or “chip” card have shown significantly lower occurrences of fraud. The United States’ slow adoption of the technology is suspected to be the reason their rate of fraud is much higher.
Different Types of Identity Theft
Before delving deeper into understanding identity theft, let us first look into some of the common terminology used in reference to these crimes:
Phishing
Misleading emails that manipulate people to enter confidential information. This could be someone pretending to be a bank representative, a health service or medical assistant, or even a credit card company.
Perhaps the most notorious incidence of phishing in recent memory was the 2016 hacking of Hillary Clinton’s presidential campaign chairman John Podesta’s e-mail account by Russian hackers. The email in question asked for Podesta’s account password, and was in fact spotted by an aide and marked as suspicious, however in the aide’s memo he made an unfortunate typo, writing that the email was “legitimate” rather than “illegitimate”. This costly error resulted in Russians gaining access to tens of thousands of emails which were the then handed over to the organization Wikileaks, who released the emails in calculated intervals over the course of the campaign, causing a public uproar and potentially costing Clinton the election.
Smishing
The same concept as phishing, but done through SMS or text messaging. This type of scam has grown more and more prevalent in recent years as criminals directly target people’s’ principal means of accessing the internet and email. A person may receive a text message requesting private information like a bank PIN number or email account password.
Another common scam is a text tailored to resemble a personal message with a request to view the presumed sender’s social media account. Clicking the link will result in the user being directed to a hazardous URL where his or her information may be compromised. The results of smishing can be just as devastating as any other identity theft, as in this 2016 scam when three Santander customers lost a combined £36,200 ($46,772) within a month, money that the bank declined to refund.
Wardriving
When someone hacks into a wireless network and installs spyware. This allows them to see what IP addresses are being used and what each device is doing, including personal information, usernames, passwords, and much more.
Surprisingly, wardriving itself is not illegal in the United States, depending on the techniques used for one to gain access to a network. There is an active debate within the internet community over the ethics of the practice.
Keylogging
Software installed either by a hacker or virus that logs every keystroke done on a computer. This key logging software reports each keystroke to the person who planted the software and can easily be deconstructed to provide them your usernames, passwords, social security information, and any other personal data they find interesting. Keylogger malware is not very complex, yet it does not have to be in order to be effective.
In 2016, cyber criminals using the keylogger program Olympic Vision were able to hack into the computers of employees of companies spanning 18 different countries in Asia, the United States and the Middle East. With a technique similar to a phishing scam, the criminals sent emails posing as business partners requesting pertinent information, yet with the malware attached. Once the malicious software was installed, it used keystroke analysis obtain all types of confidential information and login passwords.
Skimming
Devices designed to be placed over ATM and gas pump card slots that still allow the card to work, but also store the credit card information. When the person who placed it retrieves the device, the information of every credit card used during the time it was installed is then accessible by the thief. The thief then uses that information to create duplicate cards and make purchases.
The continued rise of skimming, particularly at gas stations, has prompted companies to update their payment devices with EMV technology, which reads a small chip inside the card, rather than the card’s magnetic strip. However, skimmers are still ubiquitous; typically found installed at small, isolated fueling stations at pumps farthest from the cash register.
Shoulder Surfing
When a person looks over your shoulder at an ATM or other place you may be using a debit card and entering your pin number. They can get your card account number and then learn your pin number by watching you enter it. From there, they would be able to use your debit account anywhere they want.
There is little concrete data on the frequency of shoulder surfing or the most vulnerable situations where one is susceptible to the practice, however a 2017 case study conducted by Media Informatics Group of LMU Munich, Germany concluded, based on a survey given out in the United States, Germany and Egypt, that the overwhelming majority of shoulder surfing involves strangers reading text conversations on the smartphones of strangers for the sake of boredom and curiosity without malicious intent or dangerous consequences.
Companies
In the first half of 2016, there were a record-breaking 621 mass data breaches reported worldwide. These are hackers who are attacking large companies and corporations, attempting to break into their databases and pull out any stored financial or personal information on their customers and clients.
- Target – In 2013, the US store was compromised and 40 million credit cards were stolen along with 70 million customer accounts’ information.
- Anthem – in 2015, they reported a data breach that had been going on for weeks. Someone had broken into their IT department’s records, potentially exposing each client’s name, birthdate, social security number, income data, etc.
- Home Depot – in 2014, they were attacked via a vendor through their computer’s network and 56 million credit card numbers and 53 million email addresses were stolen.
Major companies may have better security but can also be a more tempting target for potential hackers because of the wealth of information that could be retrieved if they were successful. Obviously, the attacks on Target, Anthem and Home Depot were a huge pay-off for the hackers and a catastrophic financial nightmare for the companies and, at minimum, a significant inconvenience for their customers.
How Identity Theft Happens
Emails
So how does personal information get out into dangerous territory? 23% of identity theft begins with phishing emails. Potential scammers send emails posing as a legitimate business that a person may or may not already be associated with (i.e.: a bank or credit card company) and manipulate the victim into giving them pertinent confidential information. This release of information ultimately leads to their financial accounts and/or identity being used without their permission. A phishing email is usually recognizable because the sender is asking you to verify your information through a non-secure online source. Also, generally speaking, a legitimate business would not contact you through email if there were any sort of breach of security on your account; they would either call a customer directly and/or just shut down their card.
Websites
Sometimes, scammers will set up legitimate-looking websites that are really just a ploy to acquire the user’s information. This could be in the form of a merchant website online where the user thinks they are buying an item that they never receive and, instead, have their information stolen. Other times, the scammer will make a page that looks and acts just like a well-known or reputable bank or credit institution but with a slightly different web address. The user trusts the site because it looks like a real one, enters their information, and never hears back from the site, only to find out that their information was stolen and misused.
Third parties
In addition, many people don’t realize that large corporations and popular businesses routinely sell their users’ information. These companies are required by law to put into their terms and conditions that they are able to sell your information but very few people actually look into that information when filling out forms online. By selling that information to third parties, it opens people up to spam emails, mail, phone calls, and a whole host of other problems. In recent years, major companies such as Google and Facebook have come under fire for these practices and it has becoming increasingly difficult to avoid your browsing history being exploited for market research and financial gain.
IRobot, the company behind the automated vacuum Roomba, has recently courted controversy when details leaked that it may begin to sell the data gathered by higher end Roomba models in the process of cleaning a home. Roombas use these data about the location of furniture and household appliances to more effectively tidy up a room. However, experts speculate that a Roomba would also be able to determine information about owners private lives based on lack of certain household items, or, for example, the presence of a baby chair in the living room, and sell it to advertisers who would be able to target people with alarmingly specific offers catered to their speculated needs.
Phone
In 2014, 54% of people reported that their fraudulently used information was initiated by a phone call. Most commonly, a scammer will pose as a representative from a financial institution and tell the victim that they have had suspicious activity on their account and that they need to have the victim verify information. It is only later that the victim realizes that they’ve been lied to and that they basically handed over their entire security to a stranger on the phone.
Physical collection
Another way your information can be compromised is by physical collection. If you’ve ever lost your purse or had your wallet stolen or even left a credit card behind at a restaurant, you are in danger. Additionally, personal information can be acquired by dumpster diving or digging through trash to find anything that was discarded without being shredded. Most banks and doctors’ offices have policies in place where they are required to shred personal information, but it may not occur to people that their trash from home might be gone through either by people they allow into their home or predators who could dig through your trash bin out by the road before it is collected. Any acquisition of a physical piece of identification puts someone at risk.
Information accrued from items thrown out in the trash–whether it be a gas bill or a grocery list–can allow a scammer to learn highly specific information about a homeowner’s personal life. The thief can then use the knowledge in a very convincing phishing or phone scam.
This type of scam seem far-fetched and highly unlikely, but it has been documented:
Through the years, I have been amazed at the things you can find in the trash. There is big business for identity thieves in personal garbage. More importantly, once you put your garbage out on the street for trash pickup, it usually becomes open to the public. This means that if I am so inclined, I can take that garbage and bring it home, which is exactly what I did. Each week I would snap on my rubber gloves and go through every item of trash: grocery store shopping lists, sticky notes with phone numbers, a private invitation for a little girl to a friend’s birthday party, and much more. As I continued to go through the managers’ trash, I was able to compile a list of their service providers: water bill, phone bill, gas and electric, cable, and so on. I could use this information not only to gain access into their lives but, if I wanted, to take over their lives.
Ultimately, I decided to use the billing information for the bank managers’ Internet service providers as an access point for my attack. Using the information I gained from the bills, I contacted the managers and explained that I was from that company. I told them that we were updating our services and that, for them to continue to have Internet service, they would be required to install updated software. I explained that the software would be arriving within the next week.
Because I was also able to reference their past billing information during the call, the victims never suspected a thing. Within a week, they each received a package in the mail that contained “upgrade software” and instructions. One by one, the managers installed the software.
Of course, the software they had just installed was actually malicious and designed specifically to allow me to access their computer via the Internet from anywhere in the world. Shortly after they installed the software, I was on their computers going through all their files. Within a few short days, I had usernames and passwords to corporate systems and even VPN access, which allowed me to connect directly to the financial institution’s internal network.
Prevention Plan Checklist
There are a few warning signs that personal information is or could be compromised. If a red flag is raised, a lot of damage can be avoided.
Debit/Credit Card
- Make sure that no one seems too close or nosy when entering a pin number into an ATM or other debit machine.
- Turning the card reader away from prying eyes or shielding a pin code when entering it should be done every time.
- If anyone seems nosy, wait and let them go first and then finish after they leave.
- Beware of people snooping through personal documents at home or work as this could lead to a compromise of security.
Web Safety
- Notice that there is a difference between https:// and http://. The “s” will tell you if the site is a secure, or encrypted, site. This means that potential thieves cannot easily pilfer information you provide on this site.
- In addition, a secure site will show a picture of a closed padlock next to the domain name.
- Check to see if the link presented to you in an email or text message is legitimate. Any text can become a clickable link but what it links to is obscured. Most popular browsers allow the user to hover over the link and it will reveal the true link at the bottom of the page or next to the link. This way, the user can see the link they’re presented with before clicking and accidentally exposing themselves to danger.
- Another precaution to take is to enter the link into com which, “analyzes a website through multiple blacklist engines and online reputation tools to facilitate the detection of fraudulent and malicious websites”.
- For shortened URLs, like bit.ly/ addresses, use Sucuri, which will expand the short link and search the actual destination link to make sure it is safe.
- Do not click on any attachments in emails from unknown senders as they could automatically download malware software onto your computer that can be nearly impossible to remove.
- Use trusted browsers that have built-in phishing protection. Firefox, Google Chrome, Internet Explorer and Edge are all designed to alert you of phishing websites before they are entered.
- Any site that utilizes pop-up advertisements and has obnoxious ads should raise a red flag. These sites are usually created to generate income for the owner and more filler than actual useful information. Sites like these are more likely to be used for phishing and tricking the user into downloading malware.
Phishing
- If anyone calls and requests personal information, immediately be suspicious of their identity. If they are truly from a bank, they should be able to verify your information to you, not require that you verify it with them.
- If you did not initiate the call, you can’t be sure that they are being honest about who they are. A good way to check that they are able to confirm multiple points of information about your account, including current balance or recent purchases.
- Avoid any ploy that is emotionally charged or tries to create a sense of urgency, especially where scammers might try to make you feel scared or vulnerable. This is the easiest way for them to make someone give up personal information.
- Be aware that any emails that come to your inbox from an unknown user with an emotional plea for help is likely a scam. No, there isn’t a prince in Nigeria that needs help unlocking his multi-million dollar inheritance and needs your bank account information so he can reward you with a financial gift for helping him. While cultural familiarity with the old “Nigerian Prince” scam may lead one to conclude that it’s no longer an effective means of identity theft, the FBI reports that millions continue to be taken each year in such scams, and they come in a number of guises, so beware.
- Check the email address from seemingly reputable companies. Generally, you will find a noreply@amazon.com or similar return email address. If the domain name after the @ symbol is not the corporation’s name, raise that red flag and proceed with caution.
- When using Gmail, utilize the “authentication icon for verified senders” which will show a key symbol next to verified users. This should automatically be enabled with each account.
- Be concerned if the “To:” and “Cc:” fields are addressed to multiple users. This generally means that random email addresses were generated using a computer and they’re just hoping someone bites on their scam.
- Notice misspellings or improper grammar usage. Any legitimate company will not use poor grammar and punctuation. If it sounds fishy, it probably is. Oddly enough, the obvious misspellings and typos in an email are occasionally part of the scam. By ensuring that clever people trash the email, they are isolating the most credulous targets for follow-up emails.
- Always check the domain name of the site you are on. If you think you are on twitter.com but the domain name is T V V rather than TW, it is likely a scam site setup to mirror a real site.
- If an email claims to be from law enforcement and states that you are legally required to provide information, immediately call your local authorities. Law enforcement does not use email to contact people. Ever.
Strengthen Your Data Security
- Be aware of which network you are logging into. People are susceptible of scams in public places such as coffee shops that offer open wireless networks as hackers often create “evil twin” networks with names that are nearly identical to those of the establishment’s to lure unsuspecting people into logging in and then stealing their information.
- As a rule, avoiding malware in any form is integral to security. Malware is identified as any software that is intended to damage or disable a computer. Apple computers are generally regarded as safer from malware because viruses are harder to create for their operating system along with them being less appealing because they are less used globally than windows computers.
- However, they are not impervious to spyware, which is software used to retrieve a user’s personal information by covertly stealing data from a hard drive. Installing a network protection program such as Norton Anti-Virus can block infected downloads, warn you about known social media scams and flag suspicious content. Regular operating system updates also protect against the latest spyware.
- Using encrypted sites was mentioned in passing before but it is of utmost importance and needs to be remembered. If a website begins with http:// it is NOT encrypted and any information entered on it is subject to being public information. Only sites that begin with https:// are encrypted.
- Alternatively, if you would like to take a more proactive stance at protecting online predators from getting your IP address, you could utilize a VPN, or Virtual Private Network, service.
VPN services mask your IP address and give you a generalized IP address from anywhere in the world you choose. Hackers won’t be able to use your IP address to access your confidential information any time you are utilizing this tool. Even better, it can be used on any computer, laptop, tablet or smartphone via a downloadable desktop application or smartphone app.
- Passwords should be changed every 4-6 months, especially those linked to financial and medical institutions.
- Use a complex and unique password, utilizing capitalization, numerals, and symbols wherever possible.
- Also, passwords should not be the same across the board for every login.
- As complicated as it can be to remember each password, there are mobile apps for smartphones as well as desktop applications that keep track of passwords for you.
- One highly recommended one is called LastPass, which is available for Android, iOS, and Windows Mobile for free. It not only stores your passwords in a safe place but also has a strong password generator. It is integrated into your phone’s browser and will automatically fill in login details for you. Users can choose to generate new, secure passwords and it will automatically add or update their list for them. This makes changing passwords easy to keep track of. It also syncs with your other devices seamlessly, allowing family password sharing.
- Another app option is called Keeper and is available for free on iOS, Windows Phone and Android. Not only does it keep passwords but it also can secure personal information and share it with trusted contacts directly from the app. It, too, has a password generator and can auto-fill login information. It offers iCloud backup and syncing for a charge but gives you a free 30-day trial.
- If trusting apps isn’t appealing or if you don’t own a smartphone, you could also keep a written list of usernames and passwords in a secure location.
- As technology progresses, more secure technologies are becoming available. This includes, but is not limited to, voice recognition, iris-scanning, and fingerprint recognition.
- The fingerprint is already being utilized in iPhones, the HTC One M9+, the Samsung Galaxy A8, and a handful of others.
- Even better, apps that allow purchasing or could benefit from added security are using the fingerprint software built into these platforms.
- Already, Amazon.com, eBay, the iTunes store and many others are encouraging users to utilize the fingerprint in place of a password not only for ease of use but increased security. It doesn’t hurt that it is much quicker to press your finger to the sensor than to type a username and password.
- Security extends far beyond the digital realm, too. Making sure that personal documents are shredded rather than just discarded is something most people don’t think about but should. If you don’t have a shredder, there are companies like UPS or The Office Depot that will shred documents for a nominal fee.
- Finally, make sure you review your credit report annually. Under the FACT Act, Federal law allows you a free credit report from each of the three major credit bureaus once a year. Make sure to run that report every year and review any flags for accuracy. Any incorrect information or reports can be disputed and an audit can be requested to review the information. Yes, it is time-consuming and often arduous but it is absolutely worth the effort. Each of the major credit bureaus — Equifax, Experian and TransUnion — offer a subscription service that allows you to check your score whenever you want but you can access your free reports by going to the Annual Credit Report website. This is a secure, federally-assembled website that asks you for your social security number so make sure you are on a secure computer and in a private place where no one might snoop over your shoulder while entering your information.
Recover Your Identity Checklist
Because it can be embarrassing to admit that you have been scammed, often times (and surprisingly) victims will let their pride get the best of them and will not submit a report – this what a lot of scammers hope for.
The Bureau of Justice reports that fewer than only 1 in 10 identity theft victims report the incident to the police.
- Acting quickly is integral to getting your identity back.
- The quicker you report it the sooner you can flag your accounts and avoid further damage.
- Have a physical copy of your accounts and credit/debit card information.
- Make sure it’s stored in a secure place. It’s important to have quick access to the account numbers so you can actively contact and report the lost or stolen cards.
- File a fraud alert immediately, even if misuse is only suspected.
- A fraud alert will bring up a notification when your credit is run and attempted uses will prompt verification of the user’s identity.
- This makes it more difficult for people to use your information, especially if they don’t have a copy of your driver’s license.
- You create the alert by calling one of the three major credit bureaus directly. It doesn’t matter which one is called because they are required to report the alert to the other two, saving you the trouble of calling each one directly.
- This alert will stay on your report for 90 days unless you call and remove it.
- If you are sure your identity is being misused, initiate a credit freeze with all of your compromised accounts.
- For this service, each credit bureau has to be contacted directly. A credit freeze is different from an alert because a credit freeze will make it so that banks and other companies that might open a line of credit will be denied access to your credit report, making it much more difficult for the perpetrator to open a line of credit.
- It is generally a free service but occasionally there is a nominal charge.
- When initiating your credit freeze, remember to request a copy of your credit report.
- Each bureau should give you details on how to obtain your report. Otherwise, you can obtain your credit reports online for free. Credit Karma is one of the most frequently used and trusted online credit report services in existence.
- File an identity theft report.
- This alerts federal and local authorities of the crime. This will give you the momentum you need to effectively fight any fraudulent charges and accounts.
- The first step is to file a report with the Federal Trade Commission. This division of the government is set up to help protect consumers and combat fraud, such as identity theft.
- Once the report is filed online, they provide something called an Identity Theft Affidavit, which is good to print and keep on file for your records.
- File a report with the local police.
- Calling in advance is often a good idea so they can let you know what items you should bring with you to not only verify your identity but also substantiate the theft claims. Remember to request a copy, again, for your records.
- Contact each of the credit bureaus directly.
- Each fraudulent item must have a dispute raised with the bureau it relates to. It is also wise to contact the lenders and collection agencies that are involved. As tedious and time consuming as this may be, cleaning up the mess gets harder and harder as time passes. The more effort you put into shutting down the thief immediately, will ensure there’s less mess to clean up later.
- Keep a written log of which credit bureau, lender or collection agency you contact along with who was spoken to, instructions they gave, and what time the calls were made.
- Keeping these sorts of notes not only help keep track of all the steps that each company gives to resolve the fraud but also gives the victim leverage if later there is a subsequent fraudulent charge made despite the account flags and credit freeze.
- Contact the businesses at which your identity was used falsely.
- If you noticed that your social security number was used to rent an apartment, contact the apartment complex. If your credit card information was used on Amazon.com, contact them and let them know about the fraud so that they can cancel any pending payments or shipments.
- Once the mess has been cleaned up and you’re ready to open up your accounts again, ask to begin an extended fraud alert.
- Contacting each credit bureau directly will activate this service and it allows you to have a heightened security status put on your identity as well as access to two credit reports a year, as opposed to the one allowed normally.
Find Help and Support
If you’re overwhelmed, it’s understandable. It’s almost impossible to stay ahead of the new ploys conceived every day. It might be a wise idea to consider investing in an Identity Theft Protection service. Their job is to watch your back by monitoring new accounts being opened in your name and suspicious activity on your credit accounts. It can be expensive but it’s worth it. Which company you choose depends on whether your identity has been stolen yet or not.
- If you have already suffered identity theft, you may want to consider a company like ID Watchdog ($14.95 or $19.95/month), whose primary goal is to help you recover your identity, even if the offenses happened before you joined their service.
- If protection, before identity theft happens, is the goal, a company like Identity Force might be a good option ($12.95/month with a 30-day free trial or $19.95/month).
Resources
Honestly, one of the best resources that I have found is a compiled list of 87 security experts’ Twitter accounts. They tweet daily about the latest trends, news, and security concerns to be aware of. The list can be found here. You can follow them individually or choose to follow all of them at the same time.
Another useful list comes from Heimdal security, which includes over 50 tips and tricks from various security experts.
Below you’ll find more good places to find statistics and more in-depth information on identity theft and keeping security a priority.
- How To Secure Your Social Security Number
- How To Reduce Your Risk of Identity Theft
- Identity Theft Monitoring Services
- What To Do If Identity Theft Happens To You
- Security Tips & Tricks From Top Professionals
- 87 Twitter Security Professionals To Follow Today
- Phishing Example And Red Flags – Video
- Fox News: Epidemic Of Child Identity Theft
- Bureau of Justice Statistics: Victims of Identity Theft 2014 Report
- Javelin’s Identity Fraud Report
- Warning Signs of Stolen Identity
- Reporting Identity Theft to the US Government
- Consumer Guides to Privacy And Your Rights